Application programming interfaces are critical to provide levels of system access permissions for particular groups of users, but they also present a big problem: Authorization using APIs provides a convenient backdoor for potential attacks, not to mention that APIs can become brittle and consume hours to debug and fix.
That’s why API authorization is getting a lot more attention now — including the release today of the API ThreatStats Report, which is Wallarm’s top 10 threat listing. It’s based on its analysis of more than 200 API-related leaks of the past quarter. It is an alternative to the various authentication risks from the Open Worldwide Application Security Project (OWASP), which named various kinds of authorization risks as several of its top 10 API risks. Wallarm has rolled up these different types of authorization risks into a single collection, which rises to second place in its own ranking.
“APIs are no longer just connectors; they’re the valves that control the flow of data in an organization,” wrote Wallarm’s authors. “Any leak, minor or major, can result in significant setbacks, from compliance failures to catastrophic data breaches.”
API authorizations certainly deserve more attention, as maintaining them requires a great deal of attention to the details as new applications are added or as existing relationships are modified to improve performance or to scale up their operations.
And while API problems have been in the news, they have been at the center of numerous data leaks for years, including the most recent Okta situation, along with leaks at Zoom, Apache Superset and VMware Tanzu, to name just a few more notable examples.
That’s one reason security software provider Cerbos Monday announced the public beta of a managed authorization service for application programming interfaces, called Cerbos Hub. As software stacks get more complex, they need to support more authorization decisions, methods and supply chains.
Cerbos Hub is a way for enterprise application developers to keep track of the myriad authorization policies across their application infrastructure and do so in a way that’s scalable and thorough to maximize productivity and maintain secure workflows across various processes.
“Once Cerbos Hub is implemented, developers can focus on the rest of their job without having to deal with every change in access control logic,” co-founder and Chief Executive Emre Baran told SiliconANGLE. The flow chart below shows how the Hub fits into a collection of APIs and applications:
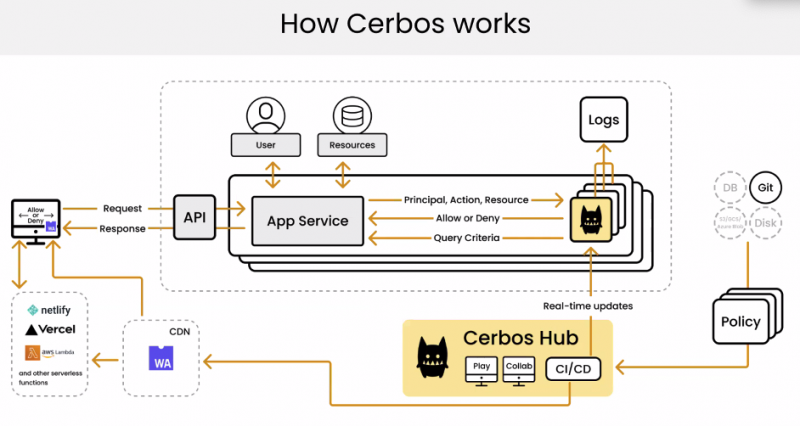
The Hub automates the authorizations across development pipelines and simplifies policy testing and implementation, according to the company. It supports a wide collection of software languages such as Ruby, Rust, Go and .Net, and can run on a wide variety of environments, including public or private clouds, serverless or on virtual machines.
It competes with open-source alternatives such as the Open Policy Project, which requires its own policy control language to set up its operations. Hub has various pricing plans, including a free tier that is limited to 500 active monthly users, and paid plans that start at $25/month.
Images: geralt/Pixabay, Cerbos
Your vote of support is important to us and it helps us keep the content FREE.
One click below supports our mission to provide free, deep, and relevant content.
Join our community on YouTube
Join the community that includes more than 15,000 #CubeAlumni experts, including Amazon.com CEO Andy Jassy, Dell Technologies founder and CEO Michael Dell, Intel CEO Pat Gelsinger, and many more luminaries and experts.
THANK YOU
"interface" - Google News
November 07, 2023 at 08:05PM
https://ift.tt/s6W1bQM
Application interfaces become more popular for authorization security exploits - SiliconANGLE News
"interface" - Google News
https://ift.tt/dCYQ0tl
https://ift.tt/wLqsaxB
Bagikan Berita Ini














0 Response to "Application interfaces become more popular for authorization security exploits - SiliconANGLE News"
Post a Comment